One of the things I find fascinating about current P2P transfer systems, like Bitcoin for instance, it's the technology behind the actual transfer, not only it's fairly simple and available technology but it's also interesting how some basic cryptographic schemes can be applied to real world value transfer problems.
In this article I will be focusing on the basic overview of how asymmetric cryptography is used.
I. Intro
So imagine you send some funds (0.0245 BTC ) to a certain address bc1qyfk0r7vs6ahwwxpy62pfvd2u90fc9k84lywe4x via any of the crypto wallets currently available.
In 10 to 30 minutes the owner of recipient address above will see the funds get confirmed and credited in the recipient's wallet, but how did it happen ?
First, The most intuitive way we might think about this transaction is more like all transactions we have always known with the common accounting system that banks and most other money handling businesses tend to generally use.
But BTC doesn't use the common account system, the process of sending in Bitcoin system is in large part a product of applied public key cryptography under the hood.
II. How Does It Work ?
Remember in the introduction part, I shared a BTC address ( bc1qyfk0r7vs6ahwwxpy62pfvd2u90fc9k84lywe4x), in this particular case, it's the receiving address of our hypothetical transaction.
In reality, that address has a 1 to 1 mapping with a public key in an asymmetric key cryptography setup
Asymmetric cryptography is a cryptographic system where keys are generated in pairs. A public one that can shared and a private one that should be kept private, in fact that's why it's even called again public key cryptography.
In this particular type of cryptographic setup, a public key is used to prove that a certain piece of data was signed by the owner of a corresponding private key, that implies that it can also be used to encrypt information with a public key and only the owner of the corresponding private key can be able to decrypt the message.
So I can distribute my public keys to people out there, not only they can check the authenticity of a particular stream of data coming from me, but they can also use the public keys shared to encrypt some bits of informations that can only be decrypted by me ( The owner of the corresponding private key).
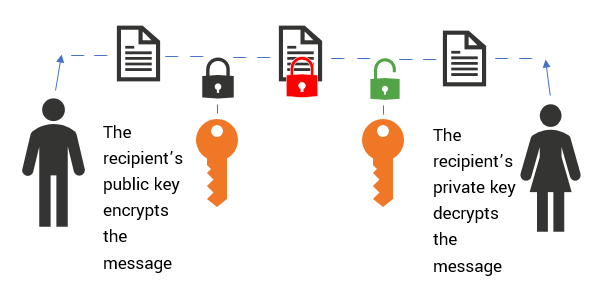
Asymmetric cryptography is a fairly vast domain , but I'm hoping the few paragraphs above gave a good overview of this particular type of cryptographic system.
Now that we have some ideas on asymmetric cryptography, let's get back to our initial address bc1qyfk0r7vs6ahwwxpy62pfvd2u90fc9k84lywe4x .
- That address corresponds to a certain public key, in this case the public key is
037bc5e8ef364e79e8342bfcfbf77e3dce01d0f164b23961d8af2fed17e35a6768.
That implies that every time funds are sent to the address above, they are actually being cryptographically locked to with that public key. - The reason those funds are cryptographically locked with that public key, is because, the owner of the public address also owns its corresponding private key and only them ( owner of the private key ) should be able to spend the funds that have been locked for that address --> public key.
III. The Analogy

The most straightforward analogy I tend to use when explaining this cryptographic scheme is mostly to think about a lock box like the one in the image above.
- Imagine you have a number of padlocks and their corresponding keys 🗝
- The padlock on the box in the image above can be considered like your public key, so you can distribute as many padlocks as you want to the potential senders. 🔒
- When the sender wants to transfer something to you, they will have to put it in a box and use the padlock you distributed to them for sealing the box.
- At the end of the day, only owner of the keys that correspond to the padlock that was used, can be able unlock those funds.
IV. Conclusion
This was a quite short article, I really hope you had a good time reading it and hopefully understood the concepts.
In case you are really interested into the concepts I touched on in this article, you can use some of the few materials I'm sharing here and many more easily available online :
- https://ee.stanford.edu/~hellman/publications/31.pdf
- https://blog.cloudflare.com/a-relatively-easy-to-understand-primer-on-elliptic-curve-cryptography/
Ciao 👋

